This is a step by step article. So every issue has been discussed in detail.
Firewall system, which can be used to ensure the best security of a network. Using it, we can monitor all types of services starting from access control in the network. For example, shutting down a particular service, applying an access restriction on a specific network, etc. We can easily implement all of these using firewall. These firewalls are usually of two types. One is software firewall and the other is hardware firewall. Notable among the hardware firewalls are: - Cisco ASA, Fortigate, Palo Alto, Barracuda, Sophos etc. In this article today we will discuss a feature of Cisco ASA Firewall.
There are two ways to access Cisco ASA Firewall. One is graphical access and the other is command line access. This graphical access is taken using HTTP protocol or Cisco ASDM tool. On the other hand, using the console port of the firewall, we can access the command line.
To get graphical access or ASDM access in the router, we must enable the HTTP protocol. The interface that we will use for ASDM access, we have to enable the HTTP protocol in that interface. By default, HTTP or ASDM access is enabled on the management port. So we can take ASDM access to that management port without any configuration.
But now if we want to get ASDM access using any interface other than that management interface, then we have to enable HTTP protocol for that interface. In this article, we will learn how to enable HTTP protocol in network interface. We can do this through two types of access. But if for some reason ASDM is not already enabled in any interface, then in that case we must do the work through command line access. Because in this case we have no way to take graphical access. So in this article we will discuss those two ways. One is ASDM access and the other is command line access.
Let us first discuss how to enable HTTP protocol in an interface using "Command Line Access".
In this tutorial, we have used “Putty” software for command line access. You can use any other terminal emulator program if you want. With access to the command line, we will go to "Global Configuration" mode. The command for that is “Config terminal”. Now your bash prompt will be like this:-
After accessing the “Global Configuration” mode, we will execute the following commands in stages.
http
server enable
http
192.168.1.0 255.255.255.0 inside
Here The first command is, to enable HTTP server mode. And the second command is, to use the "Inside" interface to enable HTTP or ASDM access from the 192.16.1.0 network. If you want, you can enable access only for a specific IP without enabling access for the entire network. Then the command will be: -
http 192.168.1.1 255.255.255.255 inside
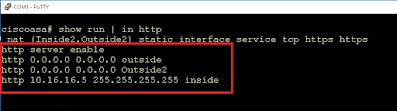
As example screenshot:-
According to this screenshot, HTTP or ASDM is enabled in all three interfaces. The first two are outside interface and the last one is inside interface. Here 0.0.0.0 means any IP address.
Now we can take graphical access using Cisco ASDM-IDM Launcher. We will gain access using the IP address or network address what we have allowed. Below is a screenshot:
If we do not have "Cisco ASDM-IDM" launcher installed, then we can install the software with http access through the browser. In this case we will open the browser and go to our allowed IP location. There we will get the option to install "Cisco ASDM-IDM" launcher. Below is a screenshot:
Let us discuss how to enable http protocol or http server in an interface using Cisco ASDM-IDM Launcher. After login using ASDM, we will go to the "Configuration" tab. Then we will select “Device Management” settings from the left panel.
Now we will expand “Management Access” from “Device Management” tree and select “ASDM / HTTPS / Telnet / SSH”.
Now we will click on the “Add” button to enable HTTP in the interface.
Here we will select our interface. Then I will write our IP address or network address and also write the subnet mask. We have used a specific IP address in our tutorial. That is why our subnet mask has been 255.255.255.255. This means that no part of this address will change. Precisely this address must be so. We have shown our "Inside" as the interface. Finally, I will close the interface by pressing "OK".
Yes, all our work is over. Now using this “inside” interface we can get HTTP access or ASDM access.