Netwatch tool, that monitors the status of a network or a link. At a certain point in time, this tool sends a ping request to a predefined network or a link. If for some reason this tool does not receive a ping response from that link or network, it sends a notification in the form of email or SMS to the system admin or user. Or maybe re-route the traffic to a different ISP or gateway.
Whenever there is a change detected in the status of the link, related action will be taken. The Netwatch tool performs this task with the help of some scripts. Whenever there is a change in the status of the link, the script related to that status will be started.
In this tutorial, we will discuss how to re-route traffic to a secondary ISP or gateway if the primary ISP or gateway gets down. At the same time, we will be discussing how to get back to the primary ISP or gateway if it comes back.
At this point, we already know that the “Netwatch” tool can monitor a gateway status or a server link by pinging that device that is located on the internet. If for any reason that link or server goes down, then this tool will disable the failed gateway link and at the same, it will enable the secondary gateway link. All the things will be done by executing the script which we have to be configured into the Netwatch tool.
In this case, no matter which link is down, it may be our router to ISP-1 link or it may be ISP-1 to their gateway link, the router will switch to secondary ISP automatically.
Now we will discuss the script that, the “Netwatch” tool will execute if the primary gateway goes down. We assume that our primary ISP gateway address is 1.1.1.1 and our secondary ISP gateway address is 2.2.2.2. We are assuming more that, the Netwatch tool will continuously send ping requests to the 8.8.8.8 server that is located on the internet using the primary ISP gateway. Also, it will send a ping request to the 8.8.4.4 server using a secondary ISP gateway. If for some reason, it didn’t get any ping response from those servers between specific periods of time, then it will disable that specific gateway. Means, If the Netwatch tool didn't get a response from the 8.8.8.8 server, then it will disable the ISP-1 gateway which is 1.1.1.1 and in the same way, if it didn't get a response from the 8.8.4.4 server, then it will disable the second ISP gateway, which is 2.2.2.2. After getting a response, it will enable it automatically.
At this point, we will add two more routes to trace the link status of ISP-1 and ISP-2. We will send 8.8.8.8 traffic via ISP-1 and 8.8.4.4 traffic via ISP-2.
To trace the ISP-1 link we will add the following route
To trace the ISP-2 link we will add the following route
Now we will go for a script.
The script for disabling primary route:-
ip route disable [find gateway="1.1.1.1"]
[Note:- If we use any comment for primary gateway entry than here we can use that comment for disabling that gateway]
ip route disable [find comment=”write_your_comment”]
For example:- ip route disable [find comment=”backup route”]
or
ip route disable [/ip route find comment="my comment"]
For example:- ip route disable [/ip route find comment="backup route"]
In the same way, the script for enabling secondary route:-
ip route enable [find gateway="2.2.2.2"]
or
ip route enable [find comment=”write_your_comment”]
For example:- ip route enable [find comment=”backup route”]
or
ip route enable [/ip route find comment="my comment"]
For example:- ip route enable [/ip route find comment="backup route"]
How to configure those script into the Netwatch tool, is shown using the picture below:-
First of all, we will open the Netwatch tool and create a rule.
Now we will create a rule and there we have to write our target server address 8.8.8.8 at the “Host” field. The rest of the things will be the default. It will send requests using our primary gateway means 1.1.1.1.
Now click on the “Down” tab and there we have to write the below code:-
ip route disable [find gateway="1.1.1.1"]
When the Netwatch tool didn't get a response from the 8.8.8.8 server, then this script will be executed. As a script, 1.1.1.1 gateway will be disabled.
Now we will go to the “Up” tab and have to write the below code:-
ip route enable [find gateway="1.1.1.1"]
When it starts getting a response from the 8.8.8.8 server, then this script will be executed. As a script 1.1.1.1 gateway will be activated.
One more thing that we have to do is, disable the associate NAT entry for that route. Because, if the NAT entry is enabled for that route, all requested traffic is going to be translated, and then it will forward to the gateway that is already disabled by the Netwatch script. As a result, all traffic should be dropped.
To disable the associate NAT we have to run another script as a part of Netwach action. We can run multiple scripts for a single Netwatch entry or we can add multiple Netwatch entries for associating that multiple scripts. Here we will use the multiple Netwach entries method.
Now we will add another entry for the 8.8.8.8 server.
Now we will go to the "Up" tab and have to write the below code:-
ip firewall nat enable numbers=0
Here, the "numbers" parameter value is represented the serial number of the NAT entry. That is:-
The script "numbers" value should be the same as your NAT entry serial number. In this example, we used 0 because of which NAT entry we are going to be disabled that NAT entry serial number is 0.
Now for the "Down" tab. Have to write the below code:-
ip firewall nat disable numbers=0
From now on, if the primary link gets down then our primary route should be disabled as well as that associate NAT should be disabled. If the link gets back, then this route entry and NAT entry would be enabled again.
Now we will add an entry for the 8.8.4.4 server. Add a new rule and write your server address means 8.8.4.4. It will send a ping request using the second ISP means 2.2.2.2.
Now click on the “Down” tab and have to write the below code:-
ip route disable [find gateway="2.2.2.2"]
When the Netwatch tool didn't get a response from the 8.8.4.4 server, then this script will be executed. As a script, 2.2.2.2 gateway will be disabled.
Now we will go to the “Up” tab and have to write the below code:-
ip route enable [find gateway="2.2.2.2"]
When it starts getting a response from the 8.8.4.4 server, then this script will be executed. As a script, 2.2.2.2 gateway will be activated.
Now, will add another entry for disabling NAT associate of that specific gateway.
Have to write the below code to the "Up" tab.
ip firewall nat enable numbers=1
Here, we used the "numbers" parameter value 1 because the serial number for that NAT entry is 1.
Now we will have to write code for the "Down" tab.
ip firewall nat disable numbers=1
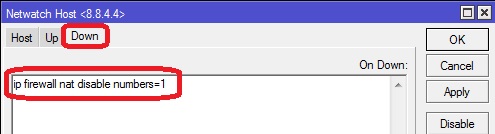
Finally, click on “Apply” and then “OK”.
Another important thing we have required to complete. If our primary link gets down then our 8.8.8.8 server should be stopped receive a response from it. Otherwise, it will not execute any code that we have written. Generally, When our Mikrotik router can't reach the 8.8.8.8 server via our primary gateway means 1.1.1.1 then it will try to reach that 8.8.8.8 server via secondary gateway means 2.2.2.2. And this time the Mikrotik router should succeed. It can reach it using a secondary gateway. That's why it will not execute any script because the link is reachable.
That's why we have to stop the Mikrotik router to reach the 8.8.8.8 server using a secondary gateway. We can do this using the firewall rule. We will create a rule that drops all the connections to reach the 8.8.8.8 server using a secondary gateway. The rule is as follows:-
ip firewall filter add chain=output dst-address=8.8.8.8 protocol=icmp out-interface=ether7 action=drop
It will be the same for the 8.8.4.4 server.
ip firewall filter add chain=output dst-address=8.8.4.4 protocol=icmp out-interface=ether8 action=drop
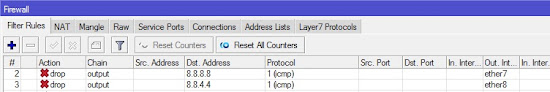
In this example, we are connected to the second ISP via the Ether7 interface. That's why we select ether7 as our output interface. And for the 8.8.4.4 server we have select out-interface ether8 because this interface is connected to our primary ISP.
From now on, if the "Netwatch" tool didn't get a ping response from the 8.8.8.8 server or 8.8.4.4 server, then it will execute those script. No matter which link is down whether it's our link or it's our ISP link, it will switch automatically. At the same time, when our primary ISP or gateway gets back, then our secondary ISP or gateway will be set as backed up automatically and our primary ISP will be activated.

















































