In this tutorial, we are going to learn how to configure the route map feature in the Cisco ASA firewall devices. The route map feature depends on the ACL to accomplish the specific task. Using ACL, it matches the specific criteria such as source and destination address, source and destination port or protocol, etc. If route-map finds any match with the predefined ACL, then it will take action based on that route map rule.
We assume that we have three local networks. Respectively they are 10.10.10.0/24, 172.16.1.0/24, and 192.168.1.0/24 network. We also assume that we have two remote gateway to reach the external networks. Respectively they are 1.1.1.1 and 2.2.2.2 gateway.
We want 1.1.1.1 will act as the default gateway. All the local networks will use this default gateway to reach the external networks except 192.168.1.0/24. We want the 192.168.1.0/24 network will forward traffic through the 2.2.2.2 gateway. The rest of the networks will use the default gateway means 1.1.1.1 gateway.
We will ASDM to configure the Cisco ASA firewall and we will go through the step-by-step process.
First of all, we will create an access list to match all the traffic that is coming from the 192.168.1.0/24 network. Then we will create a route map rule based on the access list. In the route map rule, we will set the next-hop address for the 192.168.1.0/24 network. Then we will apply this route map rule in the network interface which is connected to our local network. Because of this route map rule, whenever the firewall receives any traffic from the 192.168.1.0/24 network, it will forward all traffic through the 2.2.2.2 gateway instead of using the default gateway. Let's start the configuration process.
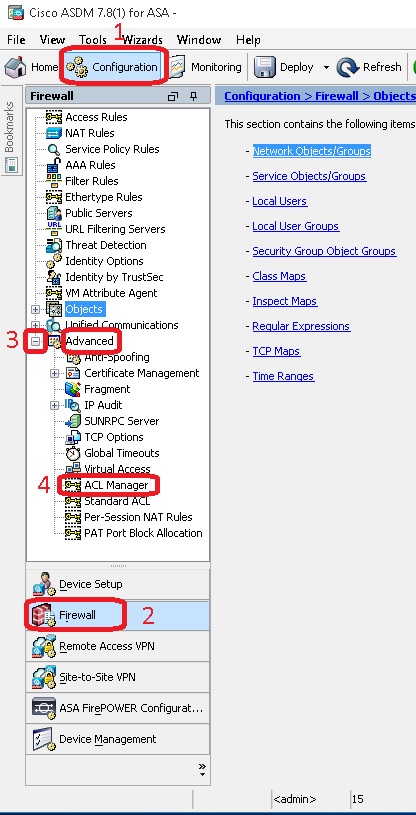
At first, we will create an access list for the 192.168.1.0/24 network to match all the traffic. After login your firewall, go to the "Configuration" tab and click on the "Firewall button". Now expand the "Advanced" tree from the firewall configuration page and select the "ACL Manager" option.
Click on the "Add" button and select the "Add ACL" from the drop-down list to add a new ACL entry. Then give a descriptive name for the ACL. We name it "Demo_ACL". Please keep in mind that, we can't use any space in this field. That's we used (_) sign instead of using space.
Now the "Demo_ACL" entry will be added to the ACL list. Right-click on the "Demo_ACL" and select "Add ACE".
Now select the "Permit" button from the "Action" field. Write your network address in the "Source" field that you want to match. According to our scenario, the network address will be 192.168.1.0/24. Keep default value for the others fields. Please make sure that the "any" is written for the destination field and the "ip" is written for the "Service" field. Finally, click on the "OK" button.
Now you will find an entry in the "ACL Manager" list.
At this time, we will create a route-map entry. For that, click on the "Device Setup" button and expand the "Routing" tree from the "Device Setup" configuration interface. Then select the "Route Maps" option. To add a new route-map entry, click on the "Add" button.
Give a descriptive name for this new rule. We name it "Demo_Rule". Again, we can't use any space in this field. Now give a sequence number for this route-map entry. We gave it 1. Then click on the "Permit" radio button for the "Redistribution" field. Now click on the "Match Clause" tab. Click on the "Match Address" check-box in the "IPv4" section. Make sure the "Access List" value is selected from the drop-down list. Now select the access list that we have just created. According to our scenario, it will be "Demo_ACL".
Now click on the "Policy Based Routing" tab. If you notified of any warning message, simply ignore it. Just click on the "Yes" button.
Now click on the "Set PBR next-hop IPv4 address" check-box. Write the remote gateway address in the "IPv4 Address" field that we want to forward all the traffic for the 192.168.1.0/24 network. According to our scenario, the remote gateway address will be 2.2.2.2. Finally, click on the "OK" button.
Our route-map rule creation process is done. Now we have to apply this route-map rule in the network interface that is connected to our local network. We assume that the "GigbabyteEthernet1/2" interface is connected to our local network.
To apply the new rule on the network interface we have to navigate the "interfaces" settings options. To open the "Interfaces" settings option we have to expand the "Interface Settings" tree. Here we will find this "Interfaces" button.
We assumed that the "GigabyteEthernet1/2" is connected to our local network. That's why we will double-click on it. Then navigate to the "General' tab and click on the route-map drop-down button. Choose "Demo_Rule" from the list, that we have created earlier. Finally, click on the "OK" button.
At last, click on the "Apply" button to affect these settings immediately.
All the configurations are done. From now on, the firewall will forward all the traffic to its default gateway that is coming from 10.10.10.0/ 24 and 172.16.1.0/24 networks. On the other hand, all the traffic will forward through the 2.2.2.2 gateway that is coming from the 192.168.1.0/24 network.










No comments:
Post a Comment